How to Decode JWT Tokens: A Step-by-Step Guide
Learn how to decode, verify, and validate JWT tokens in JavaScript, Python, C#, Java, and Go with practical examples and best practices. Discover White Owl’s free JWT Decoder tool for instant decoding.
JSON Web Tokens (JWT) have become the standard for secure authentication and data exchange in modern web applications. They are compact, self-contained, and versatile, making them ideal for APIs, single sign-on (SSO), and session management. However, working with JWTs often involves decoding them to inspect their contents, debug issues, or verify claims.
Whether you're a developer troubleshooting an authentication flow or a security engineer analyzing token structures, decoding JWTs is an essential skill. But raw, encoded JWTs can be opaque and hard to read without the right tools or methods.
In this comprehensive guide, you'll learn:
- What JWT is and why decoding it matters
- How to decode JWT manually in JavaScript, Python, C#, Java, and Go
- How to quickly decode JWT using White Owl’s free JWT Decoder
- Real-world use cases, best practices, and tips
Let’s dive in!
In this guide, we’ll cover everything you need to know about decoding JWT tokens, from manual techniques to leveraging White Owl’s free JWT Decoder. You’ll understand why decoding is crucial, how our tool makes it effortless, and how to integrate it into your workflow for faster debugging and analysis.
What is JWT and Why Decode It?
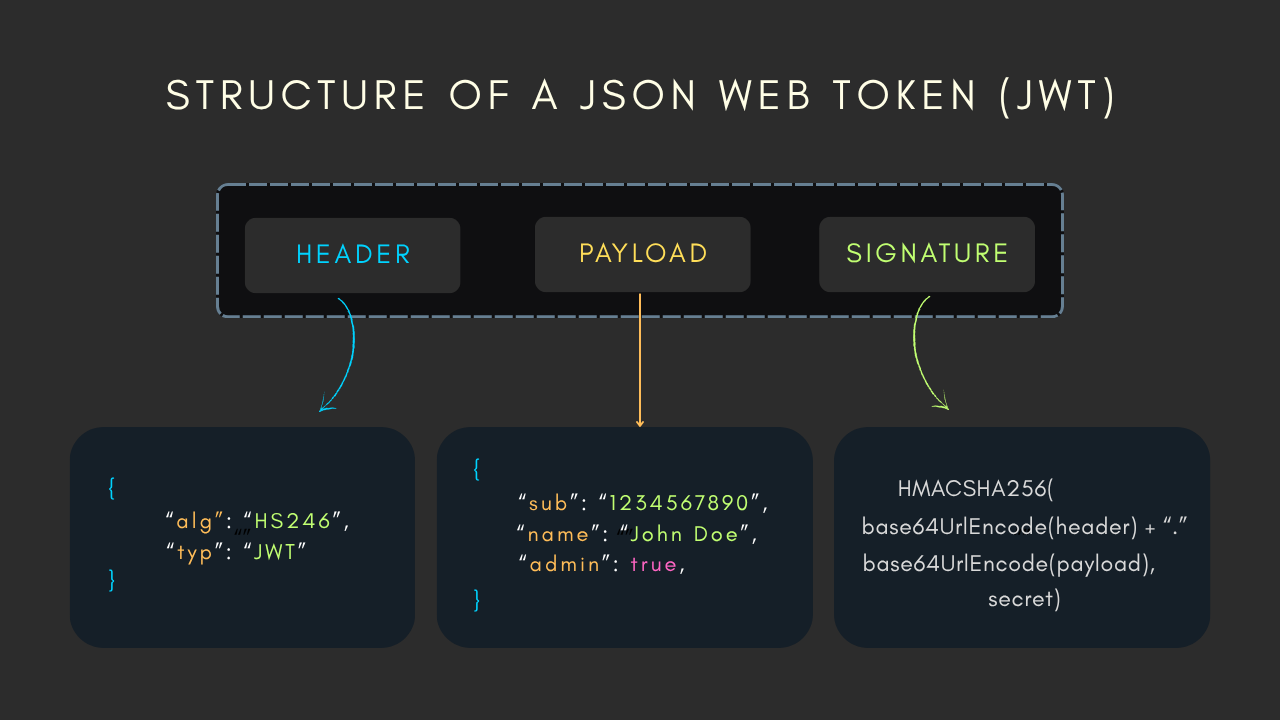
JWT, or JSON Web Token, is an open standard (RFC 7519) for securely transmitting information between parties as a JSON object. A JWT consists of three parts separated by dots: Header, Payload, and Signature.
- Header: Contains metadata about the token, such as the algorithm (e.g., HS256) and type (JWT).
- Payload: Holds the claims or data, like user ID, expiration time (exp), or custom attributes.
- Signature: Verifies the token's integrity using a secret or public key.
These parts are Base64Url-encoded, making the token compact but unreadable without decoding.
Decoding a JWT means extracting and converting the header and payload back to readable JSON, while the signature remains for verification. Here’s why decoding JWT is important:
- Debugging: Inspect claims to troubleshoot authentication failures, like expired tokens or invalid issuers.
- Security Analysis: Check for vulnerabilities, such as weak algorithms or exposed sensitive data in payloads.
- Development: Verify token structures during API integration or when building auth systems.
- Compliance: Ensure tokens adhere to standards in regulated environments.
Remember, decoding reveals the content but doesn't verify the signature—always validate signatures in production to prevent tampering.
At White Owl, our JWT Decoder not only decodes tokens instantly but also provides options for verification. But first, let’s explore manual decoding methods for a deeper understanding.
Manual JWT Decoding (Without Tools)
While online tools like White Owl’s JWT Decoder simplify the process, knowing how to decode JWT manually is valuable for scripting, automation, or environments without internet access. We’ll demonstrate this in popular languages using built-in libraries for Base64 decoding and JSON parsing.
Note: JWT uses Base64Url encoding, which replaces '+' with '-', '/' with '_', and omits padding. You’ll need to handle this in code.
JavaScript: Using atob and JSON.parse
In JavaScript (or Node.js), you can decode the header and payload like this:
function decodeJWT(token) {
const parts = token.split('.');
if (parts.length !== 3) {
throw new Error('Invalid JWT');
}
const decodeBase64Url = (str) => {
const base64 = str.replace(/-/g, '+').replace(/_/g, '/');
const padded = base64.padEnd(base64.length + (4 - base64.length % 4) % 4, '=');
return atob(padded);
};
const header = JSON.parse(decodeBase64Url(parts[0]));
const payload = JSON.parse(decodeBase64Url(parts[1]));
const signature = parts[2]; // Signature remains encoded
return { header, payload, signature };
}
// Example usage
const token = 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c';
console.log(decodeJWT(token));
Output (simplified):
{
"header": {
"alg": "HS256",
"typ": "JWT"
},
"payload": {
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022
},
"signature": "SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c"
}
This method is quick for browser-based debugging.
Python: Using base64 and json
Python’s standard libraries make JWT decoding straightforward:
import base64
import json
def decode_jwt(token):
parts = token.split('.')
if len(parts) != 3:
raise ValueError('Invalid JWT')
def decode_base64url(s):
padded = s + '=' * (4 - len(s) % 4)
return base64.urlsafe_b64decode(padded).decode('utf-8')
header = json.loads(decode_base64url(parts[0]))
payload = json.loads(decode_base64url(parts[1]))
signature = parts[2]
return {'header': header, 'payload': payload, 'signature': signature}
# Example usage
token = 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c'
print(decode_jwt(token))
Output (simplified):
{
'header': {'alg': 'HS256', 'typ': 'JWT'},
'payload': {'sub': '1234567890', 'name': 'John Doe', 'iat': 1516239022},
'signature': 'SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c'
}
Ideal for backend scripts or automation.
C#: Using System.Text.Json and Convert.FromBase64String
In C#, use .NET’s built-in features:
using System;
using System.Text;
using System.Text.Json;
class Program
{
static void Main()
{
string token = "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c";
var parts = token.Split('.');
if (parts.Length != 3)
{
Console.WriteLine("Invalid JWT");
return;
}
string DecodeBase64Url(string s)
{
string padded = s.PadRight(s.Length + (4 - s.Length % 4) % 4, '=');
padded = padded.Replace('-', '+').Replace('_', '/');
byte[] bytes = Convert.FromBase64String(padded);
return Encoding.UTF8.GetString(bytes);
}
var header = JsonSerializer.Deserialize<object>(DecodeBase64Url(parts[0]));
var payload = JsonSerializer.Deserialize<object>(DecodeBase64Url(parts[1]));
string signature = parts[2];
Console.WriteLine($"Header: {header}\nPayload: {payload}\nSignature: {signature}");
}
}
Output (simplified):
Header: {"alg":"HS256","typ":"JWT"}
Payload: {"sub":"1234567890","name":"John Doe","iat":1516239022}
Signature: SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Java: Using java.util.Base64 and org.json
Assuming org.json library for simplicity:
import java.util.Base64;
import org.json.JSONObject;
public class JwtDecoder {
public static void main(String[] args) {
String token = "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c";
String[] parts = token.split("\\.");
if (parts.length != 3) {
System.out.println("Invalid JWT");
return;
}
String decodeBase64Url(String s) {
String padded = s + "=".repeat((4 - s.length() % 4) % 4);
byte[] decoded = Base64.getUrlDecoder().decode(padded);
return new String(decoded);
}
JSONObject header = new JSONObject(decodeBase64Url(parts[0]));
JSONObject payload = new JSONObject(decodeBase64Url(parts[1]));
String signature = parts[2];
System.out.println("Header: " + header);
System.out.println("Payload: " + payload);
System.out.println("Signature: " + signature);
}
}
Output (simplified):
Header: {"alg":"HS256","typ":"JWT"}
Payload: {"sub":"1234567890","name":"John Doe","iat":1516239022}
Signature: SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Go: Using encoding/base64 and encoding/json
package main
import (
"encoding/base64"
"encoding/json"
"fmt"
"strings"
)
func main() {
token := "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c"
parts := strings.Split(token, ".")
if len(parts) != 3 {
fmt.Println("Invalid JWT")
return
}
decodeBase64Url := func(s string) ([]byte, error) {
padded := s + strings.Repeat("=", (4-len(s)%4)%4)
return base64.URLEncoding.DecodeString(padded)
}
headerBytes, _ := decodeBase64Url(parts[0])
payloadBytes, _ := decodeBase64Url(parts[1])
var header, payload map[string]interface{}
json.Unmarshal(headerBytes, &header)
json.Unmarshal(payloadBytes, &payload)
signature := parts[2]
fmt.Printf("Header: %v\nPayload: %v\nSignature: %s\n", header, payload, signature)
}
Output (simplified):
Header: map[alg:HS256 typ:JWT]
Payload: map[iat:1.516239022e+09 name:John Doe sub:1234567890]
Signature: SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Limitations of Manual Decoding:
- Error-prone for handling Base64Url variations or invalid tokens.
- Doesn't include signature verification without additional libraries (e.g., jsonwebtoken in JS).
- Time-intensive for frequent use or large tokens.
- Lacks UI for visual inspection.
For an efficient alternative, turn to White Owl’s JWT Decoder.
Step-by-Step Guide to Using White Owl’s JWT Decoder
White Owl’s JWT Decoder is a free, browser-based tool that decodes JWT tokens instantly, displaying the header, payload, and signature in a readable format. No installation or sign-up needed—perfect for quick checks.
Follow these steps:
- Access the Tool: Go to whiteowl.io/tools/jwt-decoder.
- Input Your JWT: Paste the JWT token into the input field. You can also upload a file containing the token.
- Click “Decode”: The tool automatically decodes the header and payload, showing them as formatted JSON.
- View Results: See the decoded header, payload, and raw signature. Optional: Provide a secret to verify the signature.
- Copy or Download: Copy the decoded parts or download as JSON for further use.
Example:
Input JWT:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Output:
- Header:
{ "alg": "HS256", "typ": "JWT" } - Payload:
{ "sub": "1234567890", "name": "John Doe", "iat": 1516239022 } - Signature: SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Key Features:
- Instant Decoding: Handles any valid JWT in seconds.
- Signature Verification: Optional input for HMAC secret or RSA public key.
- Error Handling: Highlights invalid tokens or syntax issues.
- User-Friendly: Clean interface with copy buttons and dark mode.
Try it now at whiteowl.io/tools/jwt-decoder!
Common Use Cases for JWT Decoding
White Owl’s JWT Decoder fits seamlessly into various workflows:
- API Debugging: Decode tokens from auth headers to check claims like user roles or expiration.
- Security Audits: Analyze payloads for sensitive data exposure or algorithm weaknesses.
- Development Testing: Verify tokens generated by your backend during integration tests.
- Incident Response: Inspect compromised tokens to understand breaches.
- Education: Teach JWT concepts by breaking down real tokens.
Example: Debugging an expired token in a REST API response. Paste the token into the tool, and instantly see the "exp" claim to confirm expiration.
Enhance your process with whiteowl.io/tools/jwt-decoder.
Tips for Effective JWT Decoding
Maximize your JWT handling with these best practices:
- Always Verify Signatures: Decoding alone isn't enough—use libraries like jsonwebtoken (JS) or PyJWT (Python) for validation.
- Handle Errors Gracefully: Check for invalid formats or expired claims in code.
- Avoid Sensitive Data in Payloads: JWT payloads are not encrypted; use encryption for confidential info.
- Use Secure Algorithms: Prefer RS256 over HS256 for asymmetric verification.
- Integrate Tools: Bookmark White Owl’s decoder for quick access; combine with our JSON Formatter for nested payloads.
- Stay Updated: Monitor JWT specs for new vulnerabilities.
These tips ensure secure and efficient token management.
Why Choose White Owl’s JWT Decoder?
Among many JWT tools, White Owl stands out:
- Free Forever: No costs, ads, or registrations.
- Speed and Reliability: Decodes complex tokens without lag.
- Intuitive UI: Easy for beginners, powerful for pros.
- Comprehensive Suite: Pair with tools like Base64 Encoder/Decoder or URL Encoder/Decoder.
- Browser-Based: Accessible on any device, no downloads.
Visit whiteowl.io/tools for more developer essentials.
Frequently Asked Questions (FAQs)
What is JWT decoding?
JWT decoding extracts the header and payload from an encoded token, converting them to readable JSON. It doesn't verify the signature.
How does White Owl’s JWT Decoder work?
Paste your token at whiteowl.io/tools/jwt-decoder, click decode, and view the results. Optionally verify signatures.
Can it handle signed JWTs?
Yes, it decodes all JWTs and supports signature verification with provided keys.
Is it secure to use online decoders?
For non-sensitive tokens, yes. Avoid pasting production tokens with private data.
What if my JWT is invalid?
The tool will display error messages, helping you identify issues.
Conclusion
Decoding JWT tokens is key to mastering authentication in modern apps. From manual methods in multiple languages to instant online tools, you now have the knowledge to handle JWTs effectively. White Owl’s JWT Decoder simplifies this, offering fast, free decoding and verification.
Ready to decode? Head to whiteowl.io/tools/jwt-decoder today. Check out our full toolset at whiteowl.io/tools and share your thoughts below!